How To Automatically Rotate AAD Application Certificates
Introduction - Why You Should Automatically Rotate Your Application Certificates
Did you know 80% of organizations have reported certificate related outage in the last two years? The reason is that computers are outnumbering humans at a ratio where manually managing certificates is impossible. One of the certificates that are easy to miss are certificate used for service to service authentication in Azure. While EZCA enables automatic Azure Key Vault certificate rotation, Azure does not currently support subject based certificate authentication, meaning that each new certificate must be registered in Azure AD before being used by an application. To solve this issue, we created a feature that automatically rotates your certificates when they are renewed. Giving you a fully automated credential rotation experience.
Enabling Azure AD Application for Automatic Certificate Rotation
To enable AAD automatic certificate rotation, we must give your application the permission of updating the credentials of the applications it owns.
Microsoft blocked it so now applications can only manage their own credentials so don’t attempt to use one application to rotate many other applications credentials.
$YourApplicationsObjectId = "<Your Application's object ID>"
$YourEnterpriseApplicationsObjectId = "<Your Application's object ID (from enterprise app)>"
#set graph permissions
$adgraph = Get-AzureADServicePrincipal -Filter "AppId eq '00000002-0000-0000-c000-000000000000'"
Write-Host "-ResourceId $($adgraph.ObjectId)"
# Manage apps that this app creates or owns (Role: Application.ReadWrite.OwnedBy)
$rdscope = "824c81eb-e3f8-4ee6-8f6d-de7f50d565b7"
Connect-AzureAD
New-AzureADServiceAppRoleAssignment -Id $rdscope -PrincipalId $YourEnterpriseApplicationsObjectId -ObjectId $YourEnterpriseApplicationsObjectId -ResourceId $adgraph.ObjectId
#Add Application as owner of itself
Add-AzureADApplicationOwner -ObjectId $YourApplicationsObjectId -RefObjectId $YourEnterpriseApplicationsObjectId
As you might notice we must get Your App’s Object ID
Getting your Application’s Object ID
- First go to the Azure portal
- Navigate to Azure Active Directory -> App registrations and select your application.
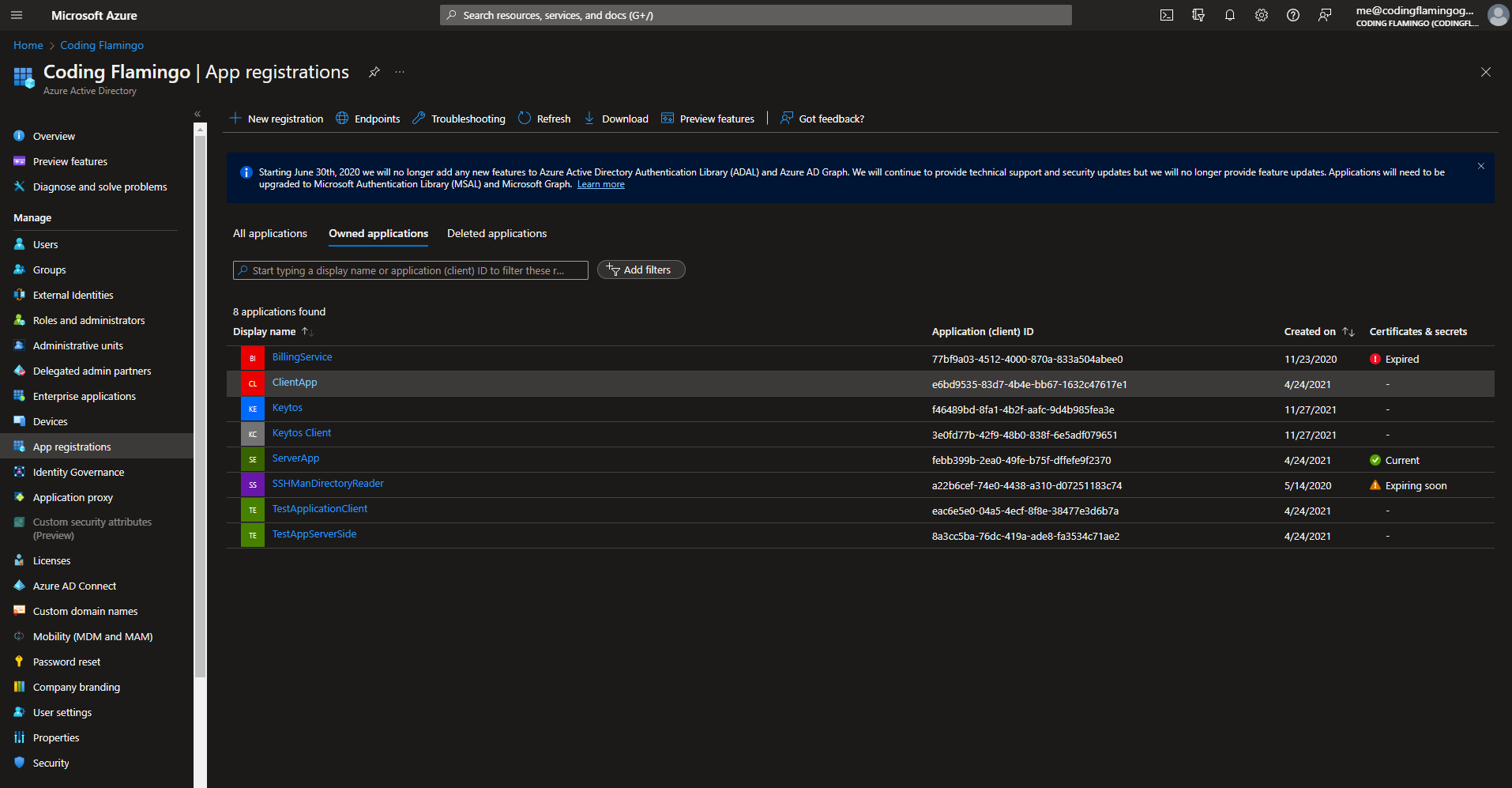
- Copy your application’s object ID.
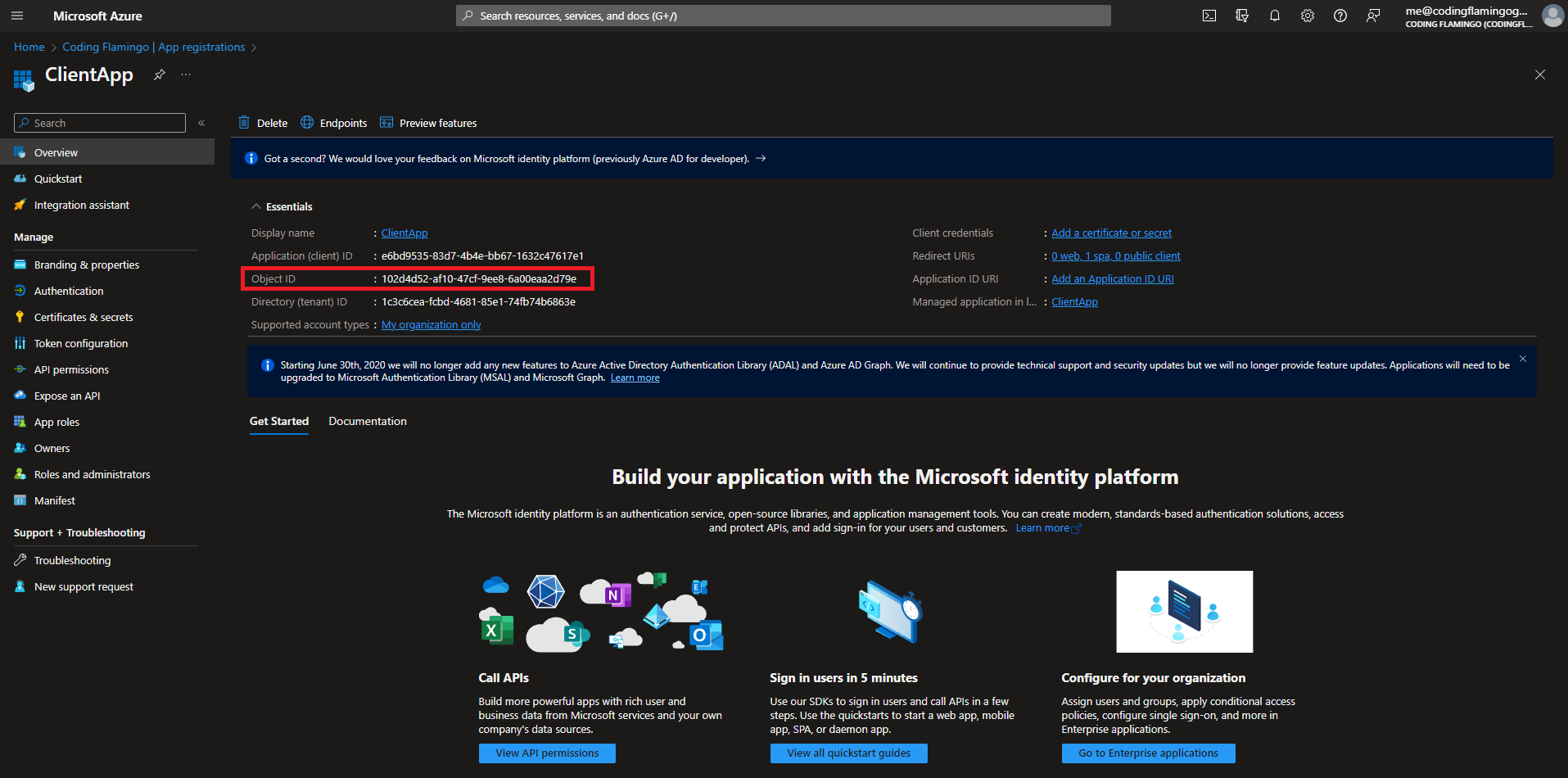
- Past it in the script as the value for
$YourApplicationsObjectId
Giving EZCA Key Vault Access
To enable this feature work, an extra permission must be given to EZCA (How to give Azure Key Vault access to EZCA) This permission is under Keys -> sign. This enables EZCA to sign the request for adding the new certificate meeting Microsoft’s key ownership attestation, while keeping your key safe in your Key Vault.
Creating The Azure AD Application Certificates
Once both pre-requisites are done, EZCA will have permissions to rotate your application’s certificates. Due to the key attestation requirements, and our zero-trust design, we currently only support this feature using EZCA’s automatic Azure Key Vault certificate rotation. Follow these steps to enable automated AAD Certificate rotation:
- Add your application ID when creating your first certificate.
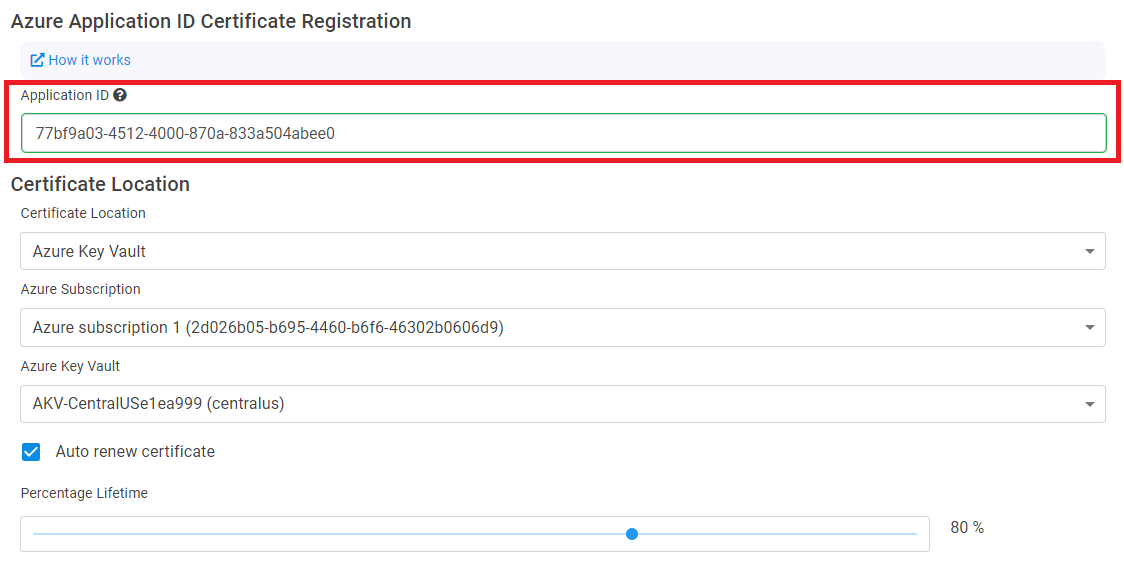
- Enable auto-rotation.
- Create your certificate.
- Add the first certificate to Your Azure application (EZCA does not have permission to add the first certificate, just to rotate it. This is a security feature to prevent EZCA from adding certificates to your application without your consent).
- We recommend manually renewing the certificate in the portal the first time to ensure the application has all the appropriate permissions.
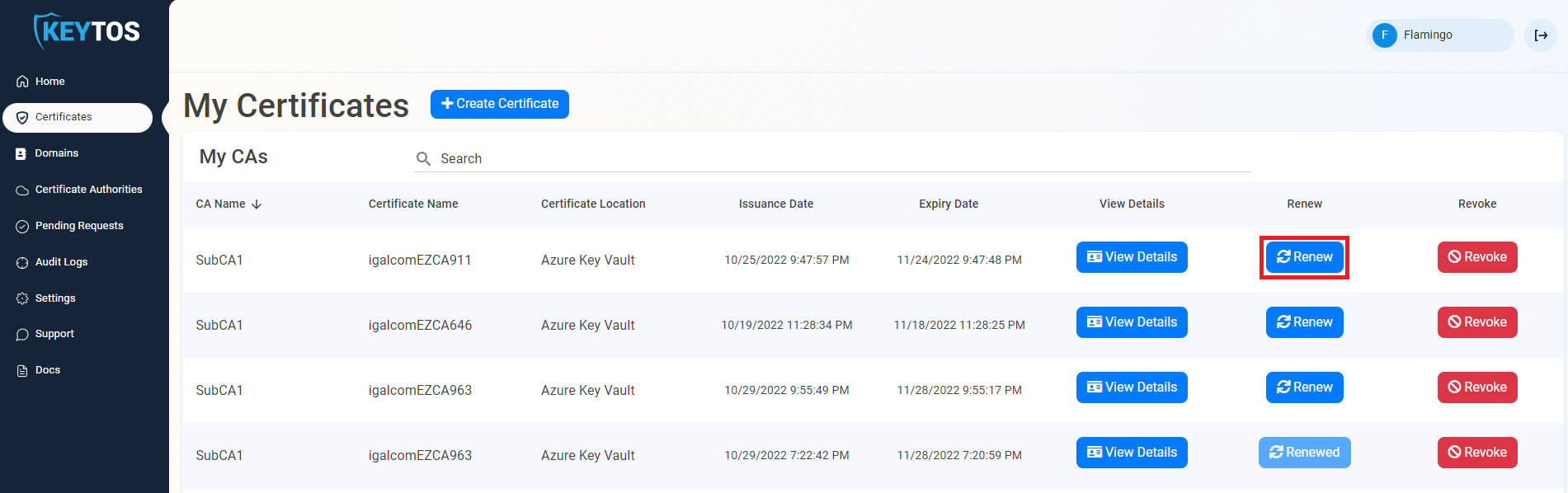
- Once you have validated that the certificate rotation is working on your application, EZCA will automatically rotate your certificate for now on.